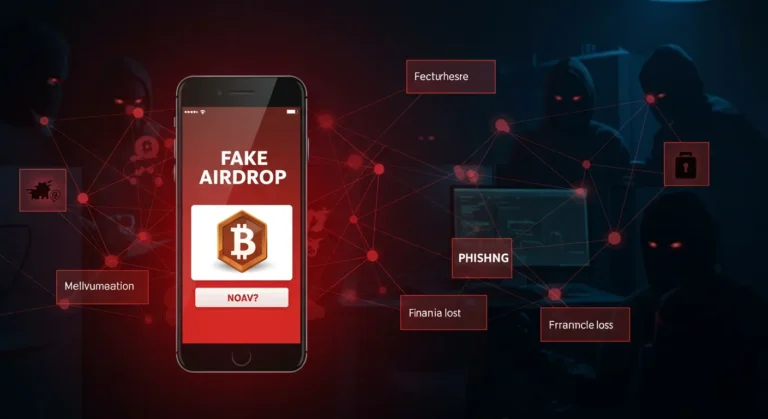
The Dangers of Free Crypto VPNs and Proxies
VPNs & Proxies are tools many of us reach for when we want privacy or to reach services that seem blocked. They can help a lot. But free versions, especially those tailored for crypto users, sometimes come with traps. In this article I’ll explain, in plain language, why free crypto VPNs and proxies can be dangerous, how to spot the red flags, and what simple steps you can take to protect your money and your privacy.
What are VPNs & Proxies and why people use them

A VPN (Virtual Private Network) and a proxy both route your internet traffic through another computer. This can hide your real IP address and help you appear to be somewhere else. People use these tools for many reasons:
- To protect privacy on public Wi-Fi.
- To access services in other countries.
- To reduce targeted ads or simple tracking.
- To try to add a layer of safety when trading crypto.
But not all VPNs and proxies are the same. Paid services spend money on secure servers, audits, and good privacy policies. Free services often must pay the bills somehow. That is where problems start.
How free services really make money
Free providers may earn from:
- Selling your browsing data to advertisers.
- Injecting ads into pages you visit.
- Running scripts that mine cryptocurrency on your device.
- Using weak or overloaded servers that expose you to attackers.
When you use these free tools for crypto activity, the stakes are higher. Your IP, device, or browser action may leak information that helps attackers. That’s why the risks of using free VPNs are more than inconvenience — they can be dangerous.
The main dangers of free crypto VPNs and proxies
Here are the most important problems people face when they use free tools for crypto work.
1. Data collection and sale
Some free services log everything you do: sites you visit, pages you open, and sometimes even form inputs. That data can be sold to brokers. If your crypto exchange logins or email appear in those records, attackers can use the information to target you later. This is a core privacy risk with free VPN services.
2. Malicious or poorly configured servers
Free proxy servers may be set up by people with bad intent. They can inspect traffic and capture passwords or private keys typed into forms. Even encrypted traffic (HTTPS) can reveal the domain you visited, and badly configured proxies can break encryption or insert tracking scripts.
3. Man-in-the-middle and traffic injection
Some proxies or VPNs intercept encrypted traffic and re-encrypt it with their own certificates. That allows them to read data if your device accepts those certificates. They may inject ads or scripts that redirect you to phishing sites. For crypto users, that can lead to phishing pages that look exactly like your wallet or exchange.
4. Logging and later compromise
Even if a free VPN claims “no logs,” the service may still keep records. Those servers can be hacked, and logs sold or leaked. If your IP and timestamps are in those logs, they can be used to piece together your activity — a real threat of using free proxy servers.
5. Device compromise and hidden mining
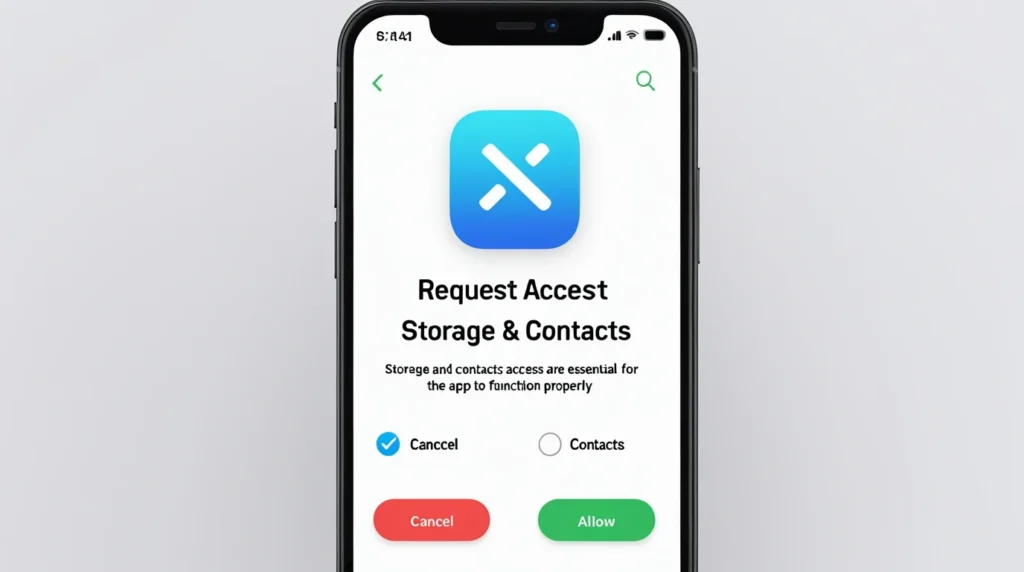
Some free services run hidden code on your device that mines cryptocurrency for the provider. That slows your device and can open new security holes. Worse, some apps request more permissions than needed and can read local storage or clipboard contents (where you might temporarily hold a wallet private key).
6. False sense of security
People using free tools for crypto often feel safer than they are. They may lower other defenses, like keeping passwords simple or saving seed phrases on the device. That false comfort creates bigger risks.
How to spot risky VPNs & proxies before you use them
You don’t need to be a tech expert to check for red flags. Here are practical checks:
- Check the business model. If a VPN is free forever, ask how they pay the servers. Ads and data sales are common.
- Read the privacy policy. If the policy is short or vague about logs and data sharing, treat it as risky.
- Look for independent audits. Reputable services often publish security audits and third-party reviews.
- Check app permissions. On phones, a VPN should not ask to read your contacts or storage. If it does, that is suspicious.
- Search for complaints. Look at forums and review sites for reports of data leaks, hidden mining, or scams.
- Avoid browser extensions posing as VPNs. Many harmful proxies are disguised as extensions that can modify web pages.
If in doubt, do not use the service for anything connected to your crypto wallets or exchanges.
Safer alternatives and simple steps to protect yourself
You can still add privacy without risking your funds. Try these practical steps.
Use a reputable paid VPN or self-hosted solution
A low-cost, well-known paid VPN is often far more secure than a free one. Alternatively, you can run your own VPN on a cloud server (a simple WireGuard or OpenVPN setup). Running your own endpoint means you control the server and logs.
Reserve a dedicated device or browser for crypto
Use one computer or browser profile only for your critical crypto activities. Do not install many extensions, and do not use free VPNs on that device. Keep seed phrases offline and never paste them into a browser.
Use hardware wallets
Hardware wallets (like Ledger or Trezor) keep private keys off the internet. Even if a free proxy captures a password or intercepts a page, the hardware wallet protects your keys.
Verify addresses manually
When sending funds, verify the public address carefully. Use a secondary method to confirm large transactions — for example, call the recipient off-chain or use a known contact method.
Revoke access and keep permissions tight
Revoke token approvals you no longer use and avoid granting unlimited allowances. That reduces the damage if a malicious site or injected script attempts to move funds.
Keep software updated
Outdated apps and browsers have known holes that proxies can exploit. Keep your systems patched and avoid installing apps from unknown sources.
Use privacy-friendly practices
Use burner wallets or fresh addresses for public activity. Don’t post your main wallet address in public forums. Small steps reduce the signals attackers use.
What to do if you suspect a VPN or proxy stole your info

If you think a free VPN or proxy caused a leak:
- Disconnect immediately. Remove the VPN app and stop using the proxy.
- Change passwords from a secure device. Do not use the compromised device for this.
- Move funds to a secure wallet (preferably hardware-based) if you still control keys.
- Revoke suspicious approvals and check exchange account activity.
- Scan your device for malware and remove unknown programs.
- Report the issue to the VPN provider and to exchanges if funds moved.
- Document everything — timestamps, screenshots, and receipts help investigations.
Acting quickly reduces harm.
Conclusion — small choices protect big things
Free tools can be tempting. I get it — we all love free. But when money is at stake, small choices matter. Free VPNs and proxies may seem harmless, but they can collect sensitive data, inject malicious code, or violate your privacy quietly. If you use crypto, make the trade-off: either invest a small amount in a reputable service, run your own server, or keep your crypto activity on a tightly controlled device without any free VPNs or proxies.
The best protection is simple: use hardware wallets, avoid public exposures, and treat free privacy services with healthy skepticism. A little care keeps your funds safe and your nights calm.
Main takeaways
- VPNs & Proxies can hide your IP, but free versions often log data or inject code.
- Risks of using free VPNs include data sale, hidden mining, and device compromise.
- Security concerns with free proxies include man-in-the-middle attacks and traffic injection.
- Dangers of using crypto VPNs are higher because leaked info may lead to direct theft.
- Privacy risks with free VPN services: unclear logging policies and weak encryption.
- Threats of using free proxy servers: malicious operators, fake browser extensions, and inserted phishing pages.
- Safer choices: paid VPNs, self-hosted VPN servers, hardware wallets, dedicated crypto devices, and careful browsing habits.
FAQ
Q: Are all VPNs and proxies unsafe for crypto?
A: No. Many reputable paid VPNs are safe. The main issue is with free services that may log or misuse data. Choose trusted providers or self-host.
Q: Can a VPN steal my crypto?
A: A VPN alone cannot directly take funds, but a malicious VPN or proxy can capture login details, inject fake wallet addresses, or run malware that leads to theft.
Q: Is a browser extension VPN safe?
A: Extensions are riskier because they can alter web pages. Avoid using extensions for crypto transactions and prefer system-level VPNs or self-hosted options.
Q: What is a self-hosted VPN?
A: It’s when you run a VPN server on a cloud host you control. It costs a small amount but gives you full control over logs and security.
Q: Should I use a free VPN for public Wi-Fi?
A: For casual browsing, a free VPN may reduce basic snooping. For crypto or sensitive tasks, do not use free VPNs — use a trusted paid VPN or your own secure connection.
Table of Contents

Hello, I’m Edmilson Dias, founder of CoinBringer. I created this platform to guide people through the fast-moving world of cryptocurrency with clarity and safety. With years of research in blockchain and digital security, my goal is to translate complex topics into practical knowledge, offering reliable tutorials, safety insights, and guidance for both newcomers and experienced users.
Discover more from CoinBringer
Subscribe to get the latest posts sent to your email.